如果在上述示例中,执行了正确的命令操作,但不能获得相应的返回结果,那么可以通过本节中的步骤逐一进行诊断。
第一步,确保正确地启用了授权,验证是否只有一个ClusterRbacConf ig实例,并且名称为default。否则,Istio将禁用授权功能并忽略所有策略。如果有多个ClusterRbacConf ig实例,请删除任何其他ClusterRbacConf ig实例,并确保只命名了一个实例default。运行以下命令列出现有ClusterRbacConf ig:
kubectl get clusterrbacconfigs.rbac.istio.io --all-namespaces NAME AGE default 19h
第二步,确保Pilot按预期工作,将授权策略转换并分发给Envoy代理。运行以下命令以打开Pilot的ControlZ:
kubectl port-forward $(kubectl -n istio-system get pods -l istio=pilot -o jsonpath='
{.items[0].metadata.name}') -n istio-system 9876:9876
正确启动之后,应当看到以下输出:
Forwarding from [::1]:9876 -> 9876 Forwarding from 127.0.0.1:9876 -> 9876
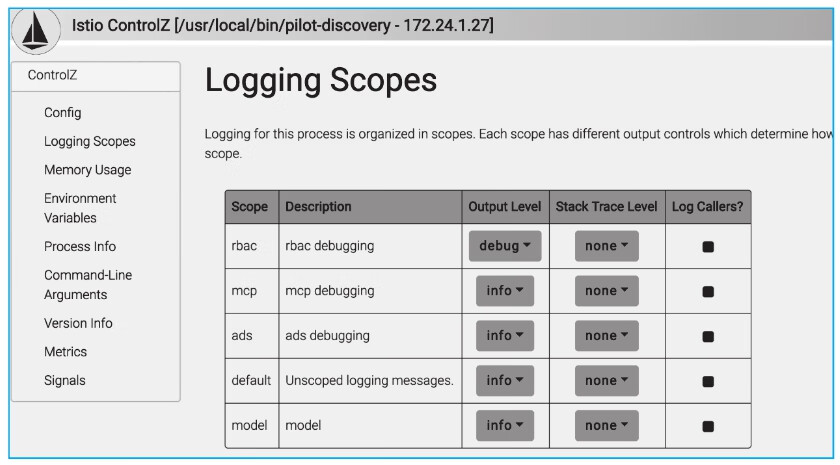
启动浏览器并打开ControlZ页面:http://127.0.0.1:9876/scopez/,将rbac输出级别更改为debug,如图7-6所示。
打印Pilot的日志并使用以下命令搜索rbac:
kubectl logs $(kubectl -n istio-system get pods -l istio=pilot -o jsonpath='{.items[0].metadata.name}') -c discovery -n istio-system | grep rbac

图7-6 ControlZ页面
可能会看到类似于如下的内容:
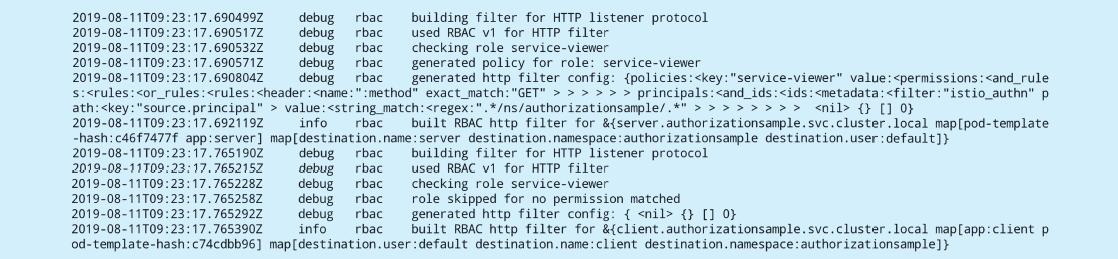
这意味着Pilot生成了server.authorizationsample.svc.cluster.local的授权策略配置,将允许任何来自于命名空间authorizationsample的其他服务使用GET方法访问它。
接着,确保Pilot将授权策略分发给Envoy代理,运行以下命令以获取服务的代理配置:
kubectl exec -n authorizationsample $(kubectl get pods -l app=server -n authori-
zationsample -o jsonpath='{.items[0].metadata.name}') -c istio-proxy -- curl local-
host:15000/config_dump -s
该日志包括一个envoy.f ilters.http.rbac过滤器,用于对每个传入请求强制执行授权策略。更新授权策略后,Istio会相应地更新过滤器。以下输出表示代理已启用envoy.f ilters.http.rbac过滤器,其规则允许任何人通过GET方法访问server.authorizationsample.svc.cluster.local:
{
"name": "envoy.filters.http.rbac",
"config": {
"rules": {
"policies": {
"service-viewer": {
"permissions": [
{
"and_rules": {
"rules": [
{
"or_rules": {
"rules": [
{
"header": {
"name": ":method",
"exact_match": "GET"
}
}
]
}
}
]
}
}
],
"principals": [
{
"and_ids": {
"ids": [
{
"metadata": {
"filter": "istio_authn",
"value": {
"string_match": {
"regex": ".*/ns/authorizationsample/.*"
}
},
"path": [
{
"key": "source.principal"
}
]
}
}
]
}
}
]
}
}
}
}
},
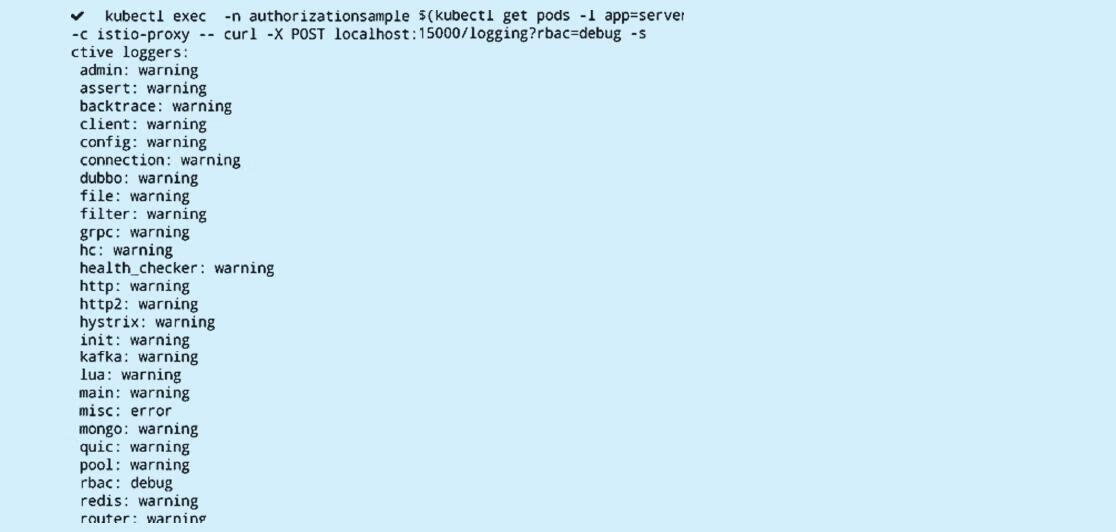
最后,确保Envoy代理最终会执行授权策略。使用以下命令打开代理中的授权调试日志记录:
kubectl exec -n authorizationsample $(kubectl get pods -l app=server -n authori-
zationsample -o jsonpath='{.items[0].metadata.name}') -c istio-proxy -- curl -X POST
localhost:15000/logging?rbac=debug -s
验证日志记录是否已经更新,应当可以得到类似于如下的输出:
使用以下命令打印Envoy代理日志:
kubectl logs -n authorizationsample $(kubectl get pods -l app=server -n authori-
zationsample -o jsonpath='{.items[0].metadata.name}') -c istio-proxy
检查输出并验证,输出日志分别显示enforced allowed或enforced denied(取决于是允许还是拒绝请求),授权策略需要从请求中提取数据。
以下输出表示GET请求中存在“/ip”请求路径,策略允许该请求执行:
[2019-08-11 09:23:29.896][25][debug][rbac] [external/envoy/source/extensions/
filters/http/rbac/rbac_filter.cc:70] checking request: remoteAddress: 172.24.0.164:
47470, localAddress: 172.24.0.43:80, ssl: uriSanPeerCertificate: spiffe://cluster.local/ns/authorizationsample/sa/default, subjectPeerCertificate: , headers: ':authority', 'server:8000'
':path', '/ip'
':method', 'GET'
'user-agent', 'curl/7.60.0'
'accept', '*/*'
'x-forwarded-proto', 'http'
'x-request-id', 'c0cac0fb-fda7-994f-9736-0be4e4c35b8f'
'x-istio-attributes', 'CkgKF2Rlc3RpbmF0aW9uLnNlcnZpY2UudWlkEi0SK2lzdGlvOi8vYXV0aG9yaXphdGlvbnNhbXBsZS9zZXJ2aWNlcy9zZXJ2ZXIKSgoYZGVzdGluYXRpb24uc2VydmljZS5ob3N0Ei4SLHNlcnZlci5hdXRob3JpemF0aW9uc2FtcGxlLnN2Yy5jbHVzdGVyLmxvY2FsCjYKHWRlc3RpbmF0aW9uLnNlcnZpY2UubmFtZXNwYWNlEhUSE2F1dGhvcml6YXRpb25zYW1wbGUKJAoYZGVzdGluYXRpb24uc2VydmljZS5uYW1lEggSBnNlcnZlcgpHCgpzb3VyY2UudWlkEjkSN2t1YmVybmV0ZXM6Ly9jbGllbnQtYzc0Y2RiYjk2LTV0dmh3LmF1dGhvcml6YXRpb25zYW1wbGU='
'x-b3-traceid', '05fa74678252dd0404cfbdca1f9b3eb1'
'x-b3-spanid', '04cfbdca1f9b3eb1'
'x-b3-sampled', '1'
'content-length', '0'
'x-forwarded-client-cert', 'By=spiffe://cluster.local/ns/authorizationsample/sa/
default;Hash=c22c2fec1fab2bf6ffbf2c79f7691473f4fe1ec4550d4370ddfdb652902b8711;Subject="";URI=spiffe://cluster.local/ns/authorizationsample/sa/default'
, dynamicMetadata: filter_metadata {
key: "istio_authn"
value {
fields {
key: "request.auth.principal"
value {
string_value: "cluster.local/ns/authorizationsample/sa/default"
}
}
fields {
key: "source.namespace"
value {
string_value: "authorizationsample"
}
}
fields {
key: "source.principal"
value {
string_value: "cluster.local/ns/authorizationsample/sa/default"
}
}
fields {
key: "source.user"
value {
string_value: "cluster.local/ns/authorizationsample/sa/default"
}
}
}
}
[2019-08-11 09:23:29.896][25][debug][rbac] [external/envoy/source/extensions/filters/http/rbac/rbac_filter.cc:110] enforced allowed
[2019-08-11T09:23:29.895Z] "GET /ip HTTP/1.1" 200 - "-" "-" 0 28 1 1 "-" "curl/
7.60.0" "c0cac0fb-fda7-994f-9736-0be4e4c35b8f" "server:8000" "127.0.0.1:80" inbound
|8000|http|server.authorizationsample.svc.cluster.local - 172.24.0.43:80 172.24.0.164:47470 outbound_.8000_._.server.authorizationsample.svc.cluster.local
通过以上步骤,可以帮助调试Istio授权,以确保应用的相应服务能够得到正确的授权并执行。